Difference between revisions of "MUD"
ArvindIOTF (talk | contribs) (Created page with "Manufacturer Usage Description (MUD) IETF Specification (MUDS) is a framework under RFC development that aims to automate Internet access control rules for IoT devices . The i...") |
ArvindIOTF (talk | contribs) |
||
| Line 23: | Line 23: | ||
A schematic form an implementation at Indiana University illustrates. | A schematic form an implementation at Indiana University illustrates. | ||
[[File:IoTSecurity MUD Arvind.png| link=https://figshare.com/articles/Manufacturer_Usage_Description_Specification_Implementation/5552923]] | [[File:IoTSecurity MUD Arvind.png| link=https://figshare.com/articles/Manufacturer_Usage_Description_Specification_Implementation/5552923]] | ||
| + | ASCII art from [https://tools.ietf.org/html/draft-lear-mud-framework-00 IETF] | ||
| + | |||
| + | ......................................... | ||
| + | . ____________ . __________ | ||
| + | . | Network | . | | | ||
| + | . | Management |----->get URI->| MFG | | ||
| + | . | System | . | Web Site | | ||
| + | . End system network |____________|<--MUD file<--<|__________| | ||
| + | . . . | ||
| + | . . . | ||
| + | . _______ _________ . | ||
| + | .| | | router | . | ||
| + | .| Thing |---->MUD URI-->| or | . | ||
| + | .|_______| | switch | . | ||
| + | . |_________| . | ||
| + | ......................................... | ||
| + | |||
| + | Figure 1: MUD Architecture | ||
Revision as of 07:24, 22 November 2017
Manufacturer Usage Description (MUD) IETF Specification (MUDS) is a framework under RFC development that aims to automate Internet access control rules for IoT devices . The intention is to specify normal and abnormal usage of a device outside the device and allow an installation to derive security controls (Access list ) and apply it. For example the posrts and servers which should be allowed to do remote service or change configuration or initiate firmware update of the device
IETF Abstract
A key presumption of the Internet architecture has been that devices are general purpose computers. By constraining the set of devices that connect to the Internet to non-general purpose devices, we can introduce a set of network capabilities that provides an additional layer of protection to those devices. One such capability is the Manufacturer Usage Description (MUD). This work builds on many existing network capabilities so as to be easily deployable by all involved. The focus of this work is primarily, but not exclusively, in the realm of security; and again primarily, but not exclusively, relating to smart objects.
IEEE
Through the simplifying assumption that a Thing has a single use or a small number of intended uses, it is possible to reduce the threat surface of the device by constraining the communication paths needed for those uses. This is accomplished using a small number of extensions to IEEE 802.1AR, a YANG model, DHCP, and IEEE 802.1AB, where a manufacturer maintains an online presence that is used inter alia to retrieve recommended configuration for a given device. This recommended configuration is used to create an access control list on a network device
CISCO Proposal
MUD allows a Universal Resource Identifier (URI) for getting ad device configuration. That URI points to a web site, either the manufacturer or the system integrator deploying devices from which the network security controller pulls the XML file<ref>YANG models [RFC6020] </ref> or JSON declaring the device’s appropriate usage. That usage file can then be merged with the existing network security policy and enforced.
MUD overview
A schematic form an implementation at Indiana University illustrates.
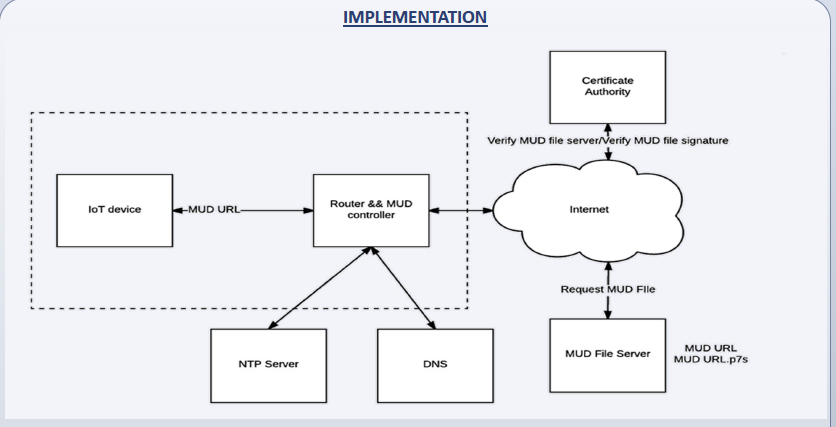 ASCII art from IETF
ASCII art from IETF
......................................... . ____________ . __________ . | Network | . | | . | Management |----->get URI->| MFG | . | System | . | Web Site | . End system network |____________|<--MUD file<--<|__________| . . . . . . . _______ _________ . .| | | router | . .| Thing |---->MUD URI-->| or | . .|_______| | switch | . . |_________| . .........................................
Figure 1: MUD Architecture