› Forums › Security › News (Security) › Icon Labs PKI Certificate management for Infineon Technologies’ OPTIGA™ Trusted Platform Module (TPM).
Tagged: SecureElement_H11
- This topic has 0 replies, 1 voice, and was last updated 6 years ago by
Curator 1 for Blogs.
-
AuthorPosts
-
-
April 28, 2017 at 6:18 am #21927
The partnership enables device manufacturers to manage PKI certificates throughout the product lifecycle using the OPTIGA™ TPM, including support for certificate injection during device manufacturing. Instead of having to manually install a certificate into each device, the device comes off the assembly line with a PKI certificate already installed.
Infineon`s OPTIGA™ TPM chip complies with the internationally recognised security standards of the Trusted Computing Group (TCG). Infineon is recognised as the supplier of security solutions for Trusted Computing.
Security is a critical requirement for the IoT, and strong device authentication, using widely adopted PKI technology, enables managed security solutions for IoT deployments. Icon Labs’ Floodgate Certificate Authority (CA) and Floodgate PKI Client allow manufacturers to incorporate certificate-based authentication using the OPTIGA™ TPM for secure key storage.
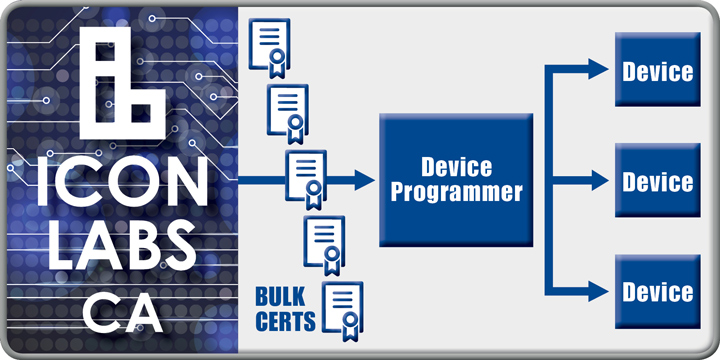
Capabilities include certificate creation during the manufacturing process using private keys stored in the TPM, certificate creation during device provisioning, and certificate management throughout the life of the device.
Icon Labs provides both the client- and server-sides of the PKI solution required to automate secure provisioning and enrollment. The Floodgate PKI Client is compatible with public and private CAs, providing the flexibility to operate a private PKI system without dependence on a public CA or to operate within the hierarchy of a public CA.
The partnership enables device manufacturers to manage PKI certificates throughout the product lifecycle using the OPTIGA™ TPM, including support for certificate injection during device manufacturing. Instead of having to manually install a certificate into each device, the device comes off the assembly line with a PKI certificate already installed.
Infineon`s OPTIGA™ TPM chip complies with the internationally recognised security standards of the Trusted Computing Group (TCG). Infineon is recognised as the supplier of security solutions for Trusted Computing.
Security is a critical requirement for the IoT, and strong device authentication, using widely adopted PKI technology, enables managed security solutions for IoT deployments. Icon Labs’ Floodgate Certificate Authority (CA) and Floodgate PKI Client allow manufacturers to incorporate certificate-based authentication using the OPTIGA™ TPM for secure key storage.
Capabilities include certificate creation during the manufacturing process using private keys stored in the TPM, certificate creation during device provisioning, and certificate management throughout the life of the device.
Icon Labs provides both the client- and server-sides of the PKI solution required to automate secure provisioning and enrollment. The Floodgate PKI Client is compatible with public and private CAs, providing the flexibility to operate a private PKI system without dependence on a public CA or to operate within the hierarchy of a public CA.
The OPTIGA™ TPM securely stores the keys, the Floodgate Factory CA Server creates device authentication certificates, and the Floodgate PKI Client enables a connection in the field to a CA for issuance of TLS and other run-time certificates. The certificates create a Root of Trust enabling secure machine-to-machine communications, using keys secured by the OPTIGA™ TPM.
“Icon Labs’ solution solves two main security challenges for the IoT,” said Steve Hanna, senior principal for Technical Marketing, of Infineon. “OEMs can easily create certificates for devices using the OPTIGA™ TPM for secured key storage, and, by automating the process, provide the scalability required as the number of IoT devices grows into the billions.”
Creating a signed certificate during manufacturing requires several steps. First, the Floodgate PKI Client requests the OPTIGA™ TPM to generate a new public-private key pair. Using this key pair, a certificate signing request (CSR) is created while the private key does not leave the TPM.
The Floodgate PKI Client sends the CSR to the Factory CA Server, which signs the request and returns a signed certificate to the PKI Client. This certificate can then be used to authenticate the device when the device is provisioned in the field.
-
-
AuthorPosts
- You must be logged in to reply to this topic.
